Over the past years, cloud computing has changed the IT sector more than any other technology. Thanks to cloud computing, organizations can now design, launch, and expand their apps more quickly than ever. However, these perks are always followed by critical cyber issues like data theft, security breaches, and hacks. Almost each cloud user must have experienced critical security incidents over the previous year.
According to the State of Cloud Security Report 2022, approximately 80% of businesses had severe cyberattack events last year, and 33% experienced a cloud data breach. According to observations, the move toward developers creating and using native cloud-based apps is redefining cloud security.
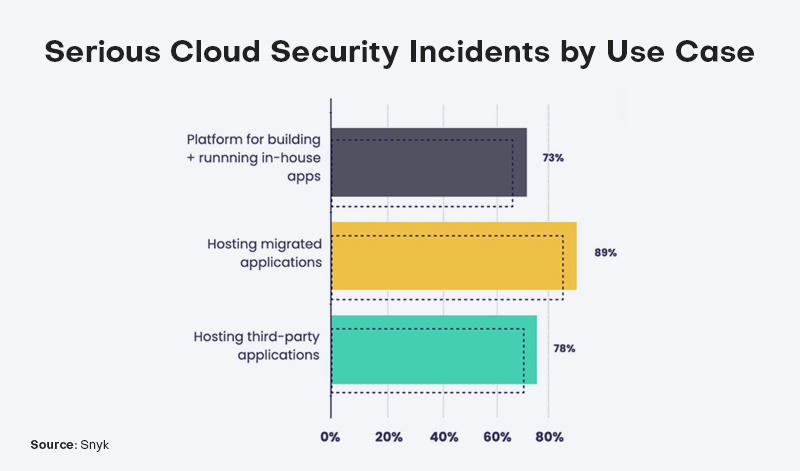
According to another cloud security study, unauthorized access is viewed as the largest security danger by 58% of organizations, and 94% of businesses have moderate to high degrees of worry regarding cloud security.
In this article, we have compiled the security concerns associated with cloud technology along with the best ways to mitigate and create a more secure cloud ecosystem.
Top Risks Leading to Security Threats & Tips to Mitigate Them
Negligence
Gartner predicts that by 2025, human errors will be, to some extent, responsible for 99% of all cloud security breaches. The danger of human mistakes is always there while developing business apps. But the risk is increased when resources are hosted on a public cloud. As the cloud is simple to use, individuals may access APIs that they are unaware of without the right restrictions, weakening network security.
All this could be avoided if companies establish robust controls to assist individuals in making the appropriate selections to reduce human error. Also, never place blame for mistakes on other people. Accuse the procedure. Create procedures and barriers to assist individuals in accessing and working with caution. Employees should receive ongoing training, be put through fake hacking scenarios to see how they react, and occasionally have their skills upgraded when sophisticated hackers emerge.
Unauthorized access
Contrary to an organization’s on-site infrastructure, its cloud-based installations are external to the network boundary and open to direct public access through web. Although this renders the infrastructure to be more accessible to both staff and consumers, it also makes it simpler for an intruder to access a company’s cloud-based services without authorization. An attacker may have the ability to get easy accessibility without an organization’s notice if security is poorly set or credentials are leaked.
To prevent unauthorized access, create a data governance structure that applies to each user account. Every authorized user should be tied directly to centralized directory services like Active Directory, which can keep track of and remove access permissions. Using third-party security technologies, you may routinely retrieve lists of users, rights, groups, and roles from cloud service settings. Your security team may then filter through and evaluate it.
To spot illegal modifications and strange behavior, you should also maintain tools for logging and event monitoring.
Misconfiguration
The cloud infrastructure’s improper setup is a major cause of data leaks. Critical corporate data and apps may be vulnerable to an attack if a company’s cloud infrastructure is poorly structured.
It can be challenging for businesses to guarantee that authorized individuals only view their data since cloud infrastructure is intended to be widely available and encourage data sharing. No visibility or management over the infrastructure inside their cloud hosting environment may worsen this problem.
In summary, misconfiguration causes major cloud security risks for enterprises, and the consequences may negatively affect regular corporate operations. Those in charge of managing the cloud solution for their company should be acquainted with the security measures offered by the cloud service provider in order to avoid errors and bugs.
Data breach
The theft of sensitive and confidential data, both accidentally and on purpose, is the biggest cloud computing danger facing enterprises today. More businesses are allowing workers to use their own devices for work without putting in place a strong security strategy, which raises the risk of data breaches. When using earlier OS versions, accessing storage services like One Drive or Dropbox via personal devices increases security threats. Threats from within are another method that private data may be exposed. Unencrypted files can make sensitive information and passwords vulnerable if an attacker obtains them.
Implement data encryption. The sensitive data shouldn’t be present in your cloud environment unless it has been encrypted. Change your password and save all of your passwords somewhere secure. Increase the number of password changes you make and be more judicious in your selection. Also, establish permissions. Not every team member needs the same degree of access to your important data. To keep the incorrect persons from accessing, assign permissions based on “need to know” criteria.
DDoS attacks
DDoS is another common cloud attack. When malicious actors target a company’s online activities using resources from several distant places, the attack is known as a DDoS or distributed denial of service. DDoS assaults often concentrate on producing attacks that interfere with network services and equipment’s normal operations.
To prevent your cloud network from DDoS attacks, get a wifi connection with extra bandwidth for your company. In order to overload its connection, attackers may use more bandwidth. Identify the flaws in your system by using web application scanning tools to scan your network and system for bugs that may be used to launch DDoS assaults.
Attack surface
The total number of external entry points into your company’s network makes up your attack surface. Consider your attack surface to be any opening or weakness that a malicious agent may utilize to access a section of your IT system. Microservice use may result in a massive increase in workload that is made available to the public. The attack surface expands with each workload. Without proper monitoring, the infrastructure may be exposed in ways that you are unaware of until an attack takes place.
Maintaining a huge attack surface for security teams is a frequent problem in the absence of strong security measures. A single user’s stolen credentials might represent a serious security risk to your whole network since there are many exposed endpoints.
Reducing the attack surface is the greatest method to minimize cybersecurity threats. The security staff may successfully safeguard the confidential information held by the business by closing off unneeded access points and protecting weak attack vectors. Managing access and user permissions, with an emphasis on revoking or modifying a user type’s degree of access, is a crucial attack surface reduction technique.
Examine network use records to identify predictable traffic patterns and bandwidth consumption, and monitor this data in your attack surface analysis.

