Two-factor authentication or 2FA is undoubtedly one of the best techniques for boosting online account security. It’s also true that higher security typically comes at the cost of less convenience. But let’s admit. Having your accounts compromised can be more frustrating than following the mundane yet extremely crucial authentication methods. In this article, we will learn more about what precisely 2FA is, why installing it is urgently necessary, some fantastic 2FA solutions, and recommended practices to adhere to while adopting a 2FA system.
What is 2FA?
In order to access a system or application, a user must provide two different identification methods in addition to their password. These identity sources are mostly email addresses and evidence of mobile phone ownership. This whole mechanism of identification is known as two-factor authentication. 2FA is a part of multi-factor authentication (MFA).
While MFA includes two or more criteria to confirm user identity, 2FA just requires two variables. Multi-factor authentication also applies offline, such as when a security door needs an eye scan and an admission card. Besides, it’s a technique to strengthen access restrictions to the more sensitive portions of web service – such as admin panels or regions that contain credit card information and/or personal data.
The ubiquitous use of 2FA in online banking, social networking sites, and shopping websites is plain to notice. Remote workers are safer thanks to 2FA, and companies and government agencies can operate more efficiently and successfully.
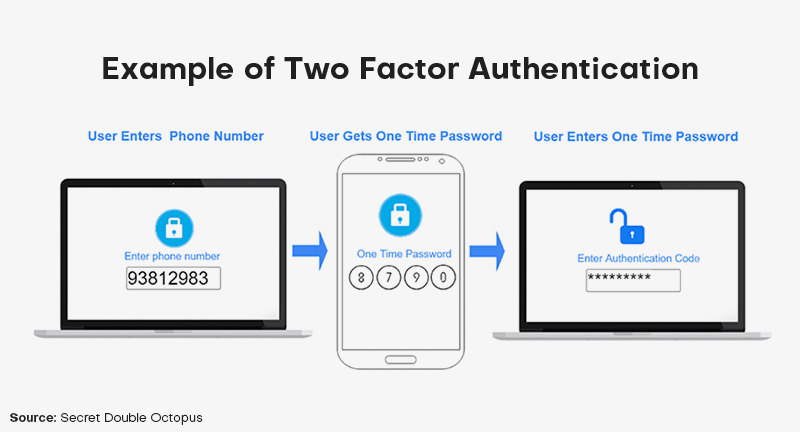
The usage of 2FA through SMS is widespread among tech behemoths like Twitter, Google, Microsoft, Apple, Facebook, and Amazon. Two-factor authentication is also being used by Internet of Things companies like Nest to protect IoT devices and enhance mobile security.
Why do we need 2FA?
We need two-factor authentication because it restricts access more successfully than using a password alone to secure your sensitive information. Even if someone manages to hack into your account, they will still require the second access factor, such as your fingerprint or an SMS verification code, in order to access your account.
Consider the possibility of someone simply discovering or guessing your password and accessing your Facebook account. Your sole line of defense against a hacker or cybercriminal looking to sell your personal information on dark web marketplaces without 2FA is a password.
Simple passwords today are ineffective against the most popular password cracking methods employed by hackers. Millions of passwords might be exposed in data breaches. That’s why, in response, organizations like Facebook and Google added 2FA to protect user information.
What therefore justifies the deployment of two-factor authentication? Even though it might sometimes take a bit longer, identity theft and having your personal information stolen are far worse than using a single password.
Two-factor Authentication Best Practices
Look for compliance and know your access points
Select a two-factor verification system based on authentication and cryptographic methods that adhere to standards. Public inspection of these requirements helps to guarantee the increased security of products that adhere to them. Moving on, you also need to check your access points. Do your users utilize the system from their workstations – at home, in public places, overseas, or elsewhere? Consider these access points when selecting a solution so that it may be used at any location where users need to authenticate.
Applying the “remember me” feature
You can request that 2FA remember you for 14 days (or more/less depending on your 2FA tool) if you discover that you need to authenticate more than once daily. Check the “Remember Me for 14 Days” checkbox when prompted to verify before completing your authentication. (You might need to click Remember Me, cancel the automated authentication, and log in normally.)
If you tick the option on your work computer, you will still need to authenticate using the authentication app if you log in on your home computer during those 14 days. This is because Remember Me is a web browser cookie that only pertains to the computer and browser that you are now using. On any computer that you routinely use and trust, you may tick Remember Me.
Compatibility with third-party solutions
Third-party solutions may advertise the newest two-factor authentication, biometrics, and other technologies. However, will they work with the company’s current infrastructure? Will the solution support the organization’s future growth, or at the very least, coexist with existing security measures? Before making a choice, stakeholders should evaluate their current PAM and IAM systems.
Choosing authentication method as per requirements
Not every access point requires the same kind of authentication methods. Solutions for two-factor authentication are rarely a one-size-fits-all proposition. Thus, it is not a smart idea to choose off-the-shelf solutions and stack them into the infrastructure. In order to design the best 2FA implementation process, organizations must think about the hardware and software they employ and how they may use it. For instance, if every employee has a device with a fingerprint scanner, it may be one of the authentication factors used.
Recovery options
The majority of authentication elements are temporal or context-based, making them transient in nature. Hardware-based tokens are very easy for users to lose. The same is true with phones, which are easily broken or misplaced. There must be procedures for users to log in even if they cannot access an authentication channel. This does not imply that the user may rely solely on the conventional password. On request, administrators must be able to switch the authentication method or offer a feature equivalent to “forgot password.”
Develop a Program
Putting anything new into practice entails more than merely installing software and disappearing. Your project has to be a part of a bigger program with resources and training accessible for everyone engaged for it to be successful.
Common 2FA tools
After learning what 2FA is and knowing its best practices, let’s check out a list of the widely used two-factor authentication tools:
- Authy: All the components we look for in a 2FA app are included in Authy. It syncs seamlessly across all your devices, is free, and operates without an internet connection. It is also quite simple to use with compatibility for the Apple Watch and plugins for Android. Any service that accepts TOTP (time-based one-time passwords) based authenticator applications can use Authy 2FA tokens for website support.
- RSA SecureID Access: One of the various multi-factor authentication options provided by the enterprise-grade two-factor authentication software RSA SecurID Access includes mobile multi-factor authentication (push notifications, one-time passwords, SMS, and biometrics), as well as conventional hardware and software tokens. The identity assurance function works by analyzing people based on various contextual elements and linking them in virtually infinite ways. The other features include biometric, single sign-on, and policy management.
- andOTP: All you might possibly need for easy and safe token storage is provided by the andOTP authenticator. For instance, andOTP’s features allow tags and token name searches. Besides, attaching a “panic button” can help reset the app and delete all tokens in an exigency.
- Okta: It’s one comprehensive solution for safely integrating technology and humans. Okta is a cloud-based identity management software for business use that integrates with almost all on-premises programs. Okta swiftly integrated with on-premise apps, IAM systems, and directories. It’s a secure and robust system. Its crucial components include single sign-on, Okta Integration Networks (OIN), provisioning, Active Directory (AD), and LDAP integration.
- VASCO Data Security: Through a fingerprint or PIN and a one-time password, users of the mobile two-factor authentication software VASCO Data Security by OneSpan may securely log in to apps on their mobile device. Push notifications or offline passcodes can be generated for users. The software is also known as DIGIPASS. Apart from multi-factor authentication and password management, it also provides a free trial and a function for user provisioning.
Is 2FA actually secure?
Single-use passwords are less safe than they once were. Hackers can use strategies like password spraying, keylogging, and brute force assaults to break your credentials in a variety of ways. Strong, complicated passwords or passphrases should always be used, but they might not always be sufficient to keep your accounts safe. Thus, authentication with two factors gets crucial. It’s a highly secure method. Although no login technique is 100% secure, 2FA significantly increases your protection against hacking attempts and data breaches. If hackers find out that you have 2FA activated, they will probably try another account, leaving yours secure.

